Last Month over 27,240,398 Malware Threats were discovered in the wild. Over 94% of this Malware was delivered via email. Phishing attacks account for more than 80% of all security incidents. While this data is troublesome it only accounts for environments that are typically contained within the four walls of Business Organizations. COVID-19 has changed the way we work and now the majority of the workforce is working from home instead of a centralized office.

In the past remote workers could be isolated or limited to only access items like email. Now that the majority of the workforce is remote there are new challenges as this remote workforce now needs more access to Business systems in order to function. Sometimes this is accomplished via a Company issued PC while others have been forced to improvise and utilize Personal Computers to do their job.

Hackers have definitely taken noticed and are working diligently to compromise remote workstations in order to obtain credentials that would give them access to vital Business Systems. Office 360 access as well and the Suite of Microsoft Cloud Offerings seem to be under the biggest attack. All a hacker has to do is craft a believable phishing email, get a user to click on what appears to be a word document or excel invoice embedded with malware, and launch malware that harvest user credentials and provide hackers unfettered access to vital Business Systems.
Armed with valid user credentials a hacker can now login to a victims Office 360 account and do reconnaissance to plan and launch a calculated attack. I have seen first-hand where an attacker has logged into a cloud environment and gathered enough intel to send a real invoice to a real client from the victim’s email account. The Hacker used the information to craft an email and ask for an update on when payment would be made on an outstanding invoice.
After reviewing the attack, it was discovered that the only data that was manipulated on the invoice was the electronic Bank Transfer Details. To prevent the victim from intercepting communications the hacker even took additional steps to hide any email communications between the client and the victim. The client in this case used the information contained in the email to make payment on a legitimate invoice.
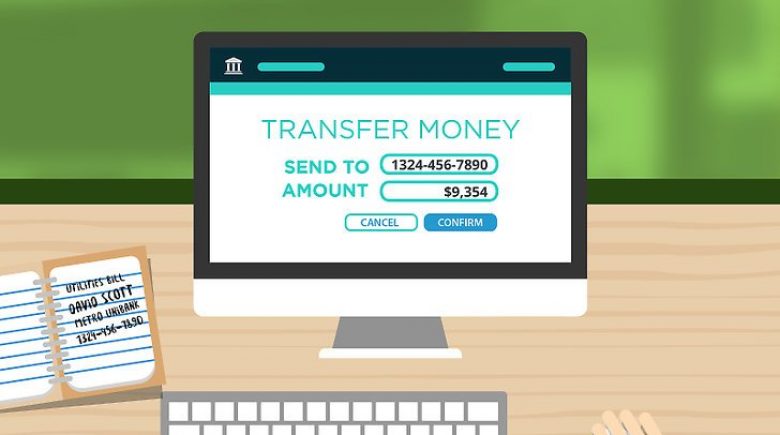
The only saving grace was the fact the clients bank flagged the transaction and stopped the transfer of over $33,000 because the destination account was new and needed verified. To be honest the fact the bank stopped the transaction is amazing.
While many believe it will not happen to them the fact is small and medium businesses are the biggest targets for Cyber Criminals. Many of the cyber-attacks against small and medium businesses go unreported or announced. These businesses fear reporting an incident affecting their business in fear will result in a larger loss of clients and bad publicity. Many choose instead to pay the ransom or pay the cost to recover and sweep the details under the rug.
So what can you do to help protect your business from attack? Well first you must implement some type of endpoint security such as application whitelisting. Second you need to have some type of email protection and filtering service. Most of all you need to have access to a team of Security Experts who can augment your existing Cyber Security Program or Help you build a new Cyber Security program from the ground up.

If you or your organization need help deploying some type of Endpoint Protection, Email Filtering Service, or building your Cyber Security Program, please reach out and I will be glad to setup a call to discuss your needs and challenges. [email protected] or 863-734-8060

